'AceDeceiver' iOS Trojan Spotted in China, Bypasses Apple's DRM Mechanism - Mac Rumors
A new iOS trojan has been found in the wild that's able to infect non-jailbroken iOS devices through PCs without the need to exploit an enterprise certificate. Named "AceDeceiver," the malware was discovered by Palo Alto Networks and is currently affecting iOS users in China.
AceDeceiver infects an iOS device by taking advantage of flaws in FairPlay, Apple's digital rights management (DRM) system. According to Palo Alto Networks, it uses a technique called "FairPlay Man-in-the-Middle," which has been used to spread pirated iOS apps in the past by using fake iTunes software and spoofed authorization codes to get the apps on iOS devices. The same technique is now being used to spread the AceDeceiver malware.
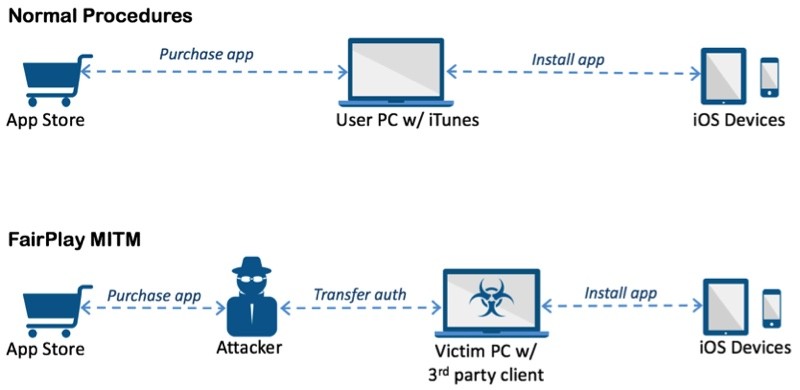
Apple allows users purchase and download iOS apps from their App Store through the iTunes client running in their computer. They then can use the computers to install the apps onto their iOS devices. iOS devices will request an authorization code for each app installed to prove the app was actually purchased. In the FairPlay MITM attack, attackers purchase an app from App Store then intercept and save the authorization code.
They then developed PC software that simulates the iTunes client behaviors, and tricks iOS devices to believe the app was purchased by victim. Therefore, the user can install apps they never actually paid for, and the creator of the software can install potentially malicious apps without the user's knowledge.
From July of 2015 to February of 2016, three AceDeceiver iOS apps were uploaded to the official iOS App Store, posing as wallpaper apps and providing attackers with a fake authorization code to use in the AceDeceiver attacks.A Windows iPhone management app called "Aisi Helper" that claimed to provide services like system backup and cleaning was installed by users in China, and it went on to install malicious iOS apps on connected devices. The apps were designed to be third-party App Stores with free content to bait users into using them and submitting their Apple IDs and passwords. Apple ID information was then uploaded to the AceDeceiver server.
Though Apple removed the original AceDeceiver iOS apps from the App Store in February (the ones used by the hackers to obtain the authorization codes), the attack remains active because attackers still have the authorization codes necessary to install fake apps on iOS devices. AceDeceiver only affects users in China, but Palo Alto N etworks believes the AceDeceiver trojan or similar malware could spread to additional regions in the future. AceDeceiver is especially insidious as it has not been patched (and could work on older versions of iOS even when patched), installs apps automatically from an infected computer, and does not require an enterprise certificate.
Palo Alto Networks has a full rundown of AceDeceiver, its history, and how it works on the Palo Alto Networks website. It's well worth reading for anyone who wants more information about the malware.
Installing software from a questionable source and get hacked? No way!"Though Apple removed the apps from the App Store in February, the attack remains active because attackers still have the authorization code,"This. This is why Apple should never bow down to the FBI in the first place, and make sure that FBI knows this that nothing is secure in this world except content in a person's head. And philosophically, Alzheimer's is one of the the virus/ malware/ trojans that can wreck havoc to that data as well, making nothing at all truly completely secure and safe.
Apple can remove the GovernmentOS but the code once created can and most likely will be out in the wild very soon. That is a risk that nobody should take.
So in order for iOS to be infected, you need to install a 'fake' iTunes to begin with?What do you expect... you do shady sh*t without fully understanding it, shady sh*t happens to you.Good old China. Can't create or do anything productive so they have to hack others. They really are one of the worst countries on the planet.
Did you really just say that China makes nothing? Since they seem to make everything , what did you mean?Is iOS getting weaker by the day?Is iOS getting weaker by the day?
Whilst it's a bit of a concern, this requires a hacked iTunes and a main in the middle between the hacked iTunes and the app store. If you're plugging your iDevices into hacked PCs and selecting "trust this device" then...iOS is by no means getting weaker (far from it, security of iOS has improved considerably even in the past 2 years), attackers are just getting more clever.
DRM screwed us??? say it ain't so!
It aint so.if there was no DRM or certificate infrastructure involved in the iPhone and iTunes this attack would be far, far more simple.
It would be a case of "plug in iPhone to PC (even non-hacked PC with genuine iTunes or non-hacked Mac), iTunes gets man-in-the-middled, you iPhone is owned"
or"Connect iPhone to dodgy wifi network, wifi operator man in the middle's apple server, you're owned"
DRM failed to protect as well as it might, but make no mistake, without it, this crap is much, much easier to do.
Didn't know the FBI is active in China.Is iOS getting weaker by the day?
There's the way in for the FBI.Good old China. Can't create or do anything productive so they have to hack others. They really are one of the worst countries on the planet.
You a Trump supporter?
0 komentar